In the realm of networking, the Open Systems Interconnection (OSI) model serves as a foundational framework that standardizes the functions of a telecommunication or computing system into seven distinct layers. Each layer has a specific role, ensuring efficient and secure data transfer. Managed IT services play a critical role in supporting all seven OSI layers, providing comprehensive solutions that keep your network robust and reliable. Here’s how:
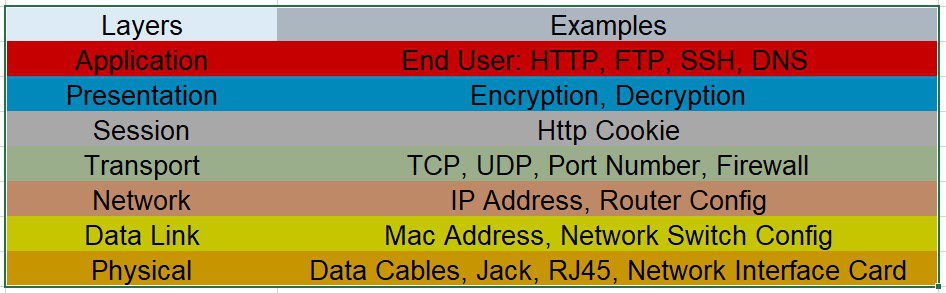
Table of Contents [hide]
- 1. Physical Layer: Hardware and Transmission Media
- 2. Data Link Layer: Reliable Data Transfer
- 3. Network Layer: Data Routing and Forwarding
- 4. Transport Layer: End-to-End Communication
- 5. Session Layer: Managing Sessions
- 6. Presentation Layer: Data Translation and Encryption
- 7. Application Layer: End-User Services
1. Physical Layer: Hardware and Transmission Media
The Physical Layer is responsible for the physical connection between devices. It involves hardware components such as cables, switches, and routers.
Support Provided:
- Hardware Management: Managed IT services ensure that all physical devices are correctly installed, configured, and maintained.
- Network Cabling: Expert cabling solutions to ensure optimal signal transmission.
- Equipment Monitoring: Continuous monitoring of hardware health to prevent failures and downtimes.
2. Data Link Layer: Reliable Data Transfer
The Data Link Layer handles error detection and correction from the Physical Layer, ensuring reliable data transfer.
Support Provided:
- MAC Address Management: Configuration and management of Media Access Control (MAC) addresses for secure device communication.
- Error Detection: Implementation of error-checking mechanisms to detect and correct data transmission errors.
- Switch Configuration: Efficient configuration and management of network switches to optimize data flow.
3. Network Layer: Data Routing and Forwarding
The Network Layer is responsible for packet forwarding, including routing through different routers.
Support Provided:
- IP Address Management: Allocation and management of IP addresses to ensure proper routing of data packets.
- Routing Configuration: Setting up and managing routing protocols (such as OSPF, BGP) to ensure efficient data paths.
- Network Security: Implementation of firewalls and intrusion detection systems to protect against unauthorized access.
4. Transport Layer: End-to-End Communication
The Transport Layer ensures complete data transfer and handles error recovery and flow control.
Support Provided:
- TCP/UDP Configuration: Setting up and managing Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) for reliable communication.
- Flow Control: Implementing mechanisms to manage data flow and avoid congestion.
- Session Management: Ensuring that data streams are properly managed and maintained.
5. Session Layer: Managing Sessions
The Session Layer manages and controls the connections between computers, handling session establishment, maintenance, and termination.
Support Provided:
- Session Establishment: Configuring protocols to establish, manage, and terminate sessions between applications.
- Authentication Services: Implementing authentication protocols to ensure secure session initiation.
- Session Maintenance: Monitoring and managing sessions to ensure they remain stable and secure.
6. Presentation Layer: Data Translation and Encryption
The Presentation Layer translates data between the application layer and the network format, ensuring data is in a readable format and handling encryption and decryption.
Support Provided:
- Data Encryption: Implementing encryption protocols to secure data during transmission.
- Data Compression: Applying data compression techniques to reduce the amount of data transmitted.
- Format Translation: Ensuring data is translated into the correct format for different applications and systems.
7. Application Layer: End-User Services
The Application Layer is the closest to the end user, providing network services directly to applications.
Support Provided:
- Application Support: Ensuring that critical business applications (such as email, web services, and databases) are always available and running smoothly.
- Service Monitoring: Continuous monitoring of application performance to ensure optimal operation.
- User Support: Providing end-user support to troubleshoot and resolve application-related issues.
Would you like to schedule a free consultation to see how we can help your business solve IT problems? Call us for a free consultation.

